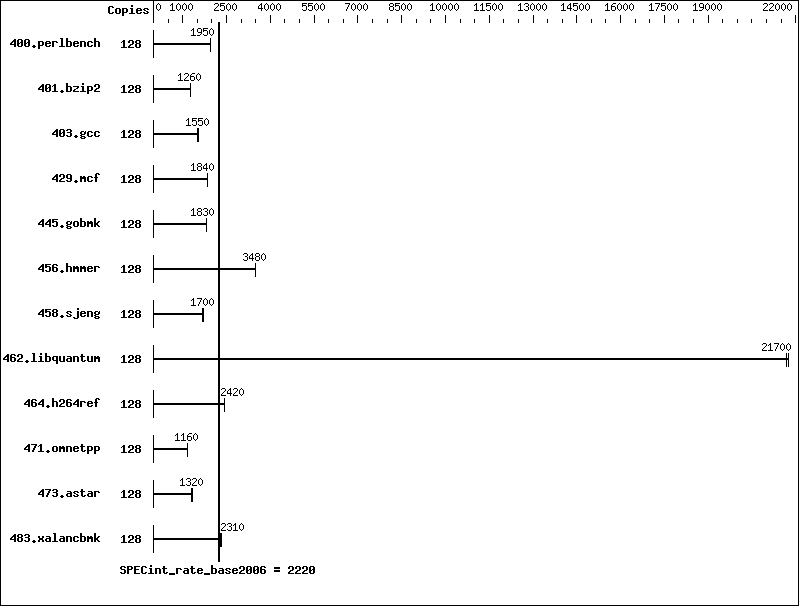
SPEC® CINT2006 Result
Copyright 2006-2018 Standard Performance Evaluation Corporation
Dell Inc.
PowerEdge R7425
(AMD EPYC 7601, 2.20 GHz)
The config file option 'submit' was used.
'numactl' was used to bind copies to the cores.
See the configuration file for details.
'ulimit -s unlimited' was used to set environment stack size
'ulimit -l 2097152' was used to set environment locked pages in memory limit
runspec command invoked through numactl i.e.:
numactl --interleave=all runspec <etc>
Set dirty_ratio=8 to limit dirty cache to 8% of memory
Set swappiness=1 to swap only if necessary
Set zone_reclaim_mode=1 to free local node memory and avoid remote memory
sync then drop_caches=3 to reset caches before invoking runcpu
Transparent huge pages were enabled for this run (OS default)
Set vm/nr_hugepages=114688 in /etc/sysctl.conf
mount -t hugetlbfs nodev /mnt/hugepages
BIOS settings:
Memory Interleaving set to Channel Interleaving
Virtualization Technology disabled
System Profile set to Custom
CPU Power Management set to Maximum Performance
Memory Frequency set to Maximum Performance
Turbo Boost enabled
C States disabled
Memory Patrol Scrub disabled
Memory Refresh Rate set to 1x
PCI ASPM L1 Link Power Management disabled
Environment variables set by runspec before the start of the run:
HUGETLB_LIMIT = "896"
LD_LIBRARY_PATH = "/home/cpu2006_o64/amd1603-rate-libs-revA/32:/home/cpu2006_o64/amd1603-rate-libs-revA/64"
The binaries were built with the x86 Open64 Compiler Suite,
which is only available from (and supported by) AMD at
http://developer.amd.com/tools-and-sdks/cpu-development/x86-open64-compiler-suite/
Binaries were compiled on a system with 2x AMD Opteron 6378 chips + 128GB Memory using RHEL 6.3
NA: The test sponsor attests, as of date of publication, that CVE-2017-5754 (Meltdown)
is mitigated in the system as tested and documented.
No: The test sponsor attests, as of date of publication, that CVE-2017-5753 (Spectre variant 1)
is mitigated in the system as tested and documented.
No: The test sponsor attests, as of date of publication, that CVE-2017-5715 (Spectre variant 2)
is mitigated in the system as tested and documented.
This benchmark result is intended to provide perspective on
past performance using the historical hardware and/or
software described on this result page.
The system as described on this result page was formerly
generally available. At the time of this publication, it may
not be shipping, and/or may not be supported, and/or may fail
to meet other tests of General Availability described in the
SPEC OSG Policy document, http://www.spec.org/osg/policy.html
This measured result may not be representative of the result
that would be measured were this benchmark run with hardware
and software available as of the publication date.